IT Knowledge Base
How to stop/start and disable/enable firewall on Oracle Linux 7.
Fedora 18 introduced firewalld as a replacement for the previous iptables service. Since RHEL7 and Oracle Linux 7 are based on Fedora 19, the switch from iptables service to firewalld is now part of the Enterprise Linux distributions.
The firewall on Oracle Linux 7 system is enabled by default. Normally there should not be a need to disable firewall but it may be quite handy for testing purposes etc. The firewall runs as firewalld daemon. Bellow command can be used to check the firewall status:
From the above output we can see that the firewall is enabled, which means it will start automatically after reboot and that is also current active. Furthermore, you can even check all currently applied rules with:
You need to distinguish between the iptables service and the iptables command. Although firewalld is a replacement for the firewall management provided by iptables service, it still uses the iptables command for dynamic communication with the kernel packet filter (netfilter). So it is only the iptables service that is replaced, not the iptables command. That can be a confusing distinction at first.
The firewall on Oracle Linux 7 system can be stopped by a following command:
Stopped firewall will start again after system’s reboot. To start firewall use the following command:
In order to completely disable OL7 firewall, so it would not start after reboot, run:
Now the firewall would not start after system’s reboot. To enable the firewall again run:
Linux Firewall (firewalld, firewall-cmd, firewall-config)
Fedora 18 introduced firewalld as a replacement for the previous iptables service . Since RHEL7 and Oracle Linux 7 are based on Fedora 19, the switch from iptables service to firewalld is now part of the Enterprise Linux distributions. This article is a rework of the previous Linux Firewall article, bringing it up to date.
You need to distinguish between the iptables service and the iptables command. Although firewalld is a replacement for the firewall management provided by iptables service , it still uses the iptables command for dynamic communication with the kernel packet filter (netfilter). So it is only the iptables service that is replaced, not the iptables command. That can be a confusing distinction at first.
Reverting to the iptables Service
If you are not ready to make the break to firewalld , you can still use the iptables service by issuing the following commands.
From this point forward, firewall administration will be similar to that described here.
The rest of this article assumes you are going to use firewalld .
Installation
Most installations will include the firewall functionality, but if you need to manually install it, do the following.
Make sure the service is started and will auto-start on reboot.
You can check the current status of the service using the following command.
To disable the firewall, run the following commands.
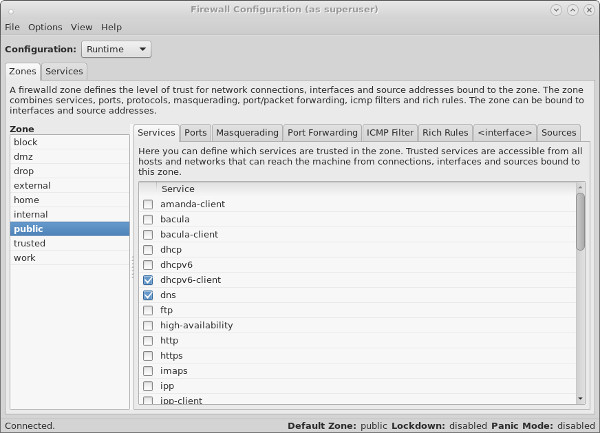
firewall-config
The GUI screen to control the firewall is available from the menu.
- Fedora : System > Administration > Firewall
- RHEL7/OL7 : Applications > Sundry > Firewall
Alternatively, if can be started from the command line using the firewall-config command. If it is not already present, it can be installed using the following command.
Once started, the «Configuration:» drop-down allows you to decide if you are modifying currently running settings (Runtime) or those saved for future use (Permanent). You can also configure basic trusted services, such as SSH, FTP and HTTP, by putting a tick in the appropriate checkbox. All changes are applied immediately.
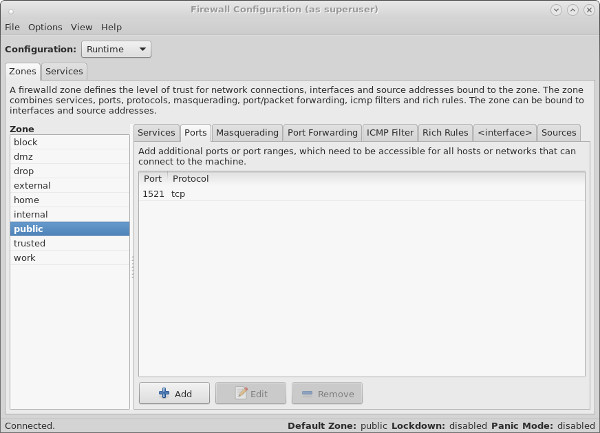
The «Ports» tab allows you to manually open ports that are not covered in the «Trusted Services» section.
Remember, changes to the runtime configuration will be lost after the next reboot. If in doubt, make all changes to the permanent configuration and reload the runtime configuration using the «Options > Reload Firewalld» menu option.
firewall-cmd
In addition to the GUI interface, the firewall rules can be amended directly using the firewall-cmd command. The full extent of the firewall configuration is beyond the scope of this article, so instead a few specific examples will be given to allow you to get a feel for it. This article also assumes you have a single network interface and are happy to keep it set to the default zone (public).
The firewall-cmd usage notes are displayed when you use the «-h» or «—help» options.
Check the current top-level firewall configuration using the following commands.
Lock down and unlock the firewall using the following commands.
Reload the runtime configuration from the permanent files using the following command.
The firewall comes with predefined services, which are XML files is the «/usr/lib/firewalld/services/» directory.
You shouldn’t edit these. Instead, copy a specific service file to the «/etc/firewalld/services/» directory and editing it there. The firewalld service always uses files in «/etc/firewalld/services/» directory in preference to those in the «/usr/lib/firewalld/services/» directory. Remember to reload the config after making any changes.
As with the GUI interface, you need to decide if you want to make changes to either the runtime configuration, permanent configuration or both. If you want to set both the runtime and permanent configuration you have two choices. Set them both independently, or set the permanent configuration and reload the firewall.
Add an existing service to a zone.
All subsequent examples will assume you want to amend both the runtime and permanent configuration and will only set the permanent configuration and then reload the runtime configuration.
Once you’ve amended the default configuration, the «/etc/firewalld/zones/public.xml» file will be created. You can manually amend this file, but you will need to issue a reload for the changes to take effect.
Check the services in a zone.
Remove a service from a zone.
Open a specific port or range in a zone, check its runtime and permanent configuration, then remove it.
Rich rules allow you to create more complex configurations. The following command allows you to open HTTP access to a specific IP address.
The «/etc/firewalld/zones/public.xml» file now contains the rich rule.
The rule can be removed directly from the XML file, or removed using the «—remove-rich-rule» option.
The following example opens and closes port 8080 for a specific source IP address using a rich rule.
Backups and Transfers of Firewall Configuration
As all non-default configuration is placed under the «/etc/firewalld/» directory, taking a copy of the contents of this directory and its sub-directories constitutes a backup of the firewall configuration.
Not surprisingly, transferring the contents of this directory will allow you to duplicate the firewall configuration in other servers.
Quick Database Setup
If you are using the server as an Oracle database server, you will probably want to make sure the SSH and Oracle listener ports are accessible. You could lock these down to specific source IP addresses, but for a quick setup, you could just do the following, where «1521» is the port used for the listener.
Oracle Database 12c on Oracle Linux 6 – Step 5: Disable the Firewall, iptables and SELINUX
Part of this series of posts: Oracle 12c on Oracle Linux 6
Click Other….
Enter root as the username and click Log In.
Enter rootroot as the password (or the password you used earlier) and click Log In.
Check Do not show me this again and click Close.
Note:
Or don’t check Do not show me this again if you want to see this warning each time you log in to the X-Windows GUI as root. In general you shouldn’t be logging into the GUI as root. We’re going to do so because it will be easier to use some of the system tools (no pop-ups to log in again as root) to configure our system.
Select System -> Administration -> Firewall from the menu bar.
Click Close.
Click Disable.
Click Apply.
Click Yes.
Select File -> Quit to close the Firewall Configuration.
Select System -> Administration -> Services from the menu bar.
Select the ip6tables service and click Disable.
Select the iptables service and click Disable.
Select Program -> Quit to close the Services Configuration.
Right-click the desktop and select Open in Terminal to open a terminal window.
Type the following command and press Enter.
gedit /etc/sysconfig/selinux
Note:
You can use Ctrl-Shift + (the plus key) to change the font size of your terminal windows. I also resize my windows to fill the whole screen. Between major command groupings I’ll also type clear to remove the previous commands from the window and start fresh.
Change SELINUX=enforcing to SELINUX=disabled.
Note:
Why disable SELINUX? According to user 546612 on the Oracle.com forums:
Depending on what pieces of Oracle you are using, there are setuid/setgid issues, there are network interactions, there is fork/exec permission stuff, shared memory, etc. Some stuff in Oracle runs as root, especially if you do RAC. There is a whole whack of IPC.
Note that Redhat recently published a paper that describes how to make SELINUX work with Oracle 11g R2 on Redhat which should work on Oracle Linux too. Since this is a test system, disabling was easier…
http://www.redhat.com/resourcelibrary/reference-architectures/deploying-oracle-11gr2-on-rhel-6
Make sure your SELINUX line reads SELINUX=disabled and Click Save.
Select File -> Quit from the menu to close gedit.